You now need to change the forwarding rules for Ips on the Server-side.
$ sudo nano /etc/sysctl.conf
Find the "net.ipv4.ip_forward" section and remove the "#" to uncomment the command.
Some of the firewall rules must be changed to route the Client connections correctly.
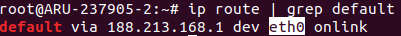
$ ip route | grep default
Make a note of the name after "dev" (in the image the name is "eth0").
$ sudo nano /etc/ufw/before.rules
Add the commands as shown below, replacing "eth0" with the name of your network interface.
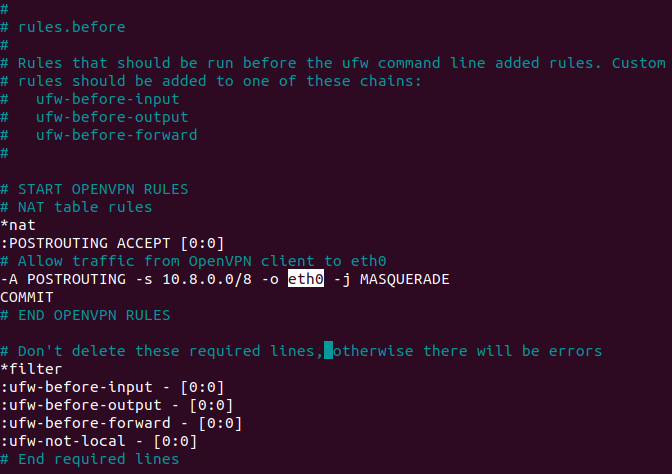
Save and exit.
$ sudo nano /etc/default/ufw
Edit the "DEFAULT_FORWARD_POLICY" parameter with "ACCEPT".
Enable port 1194 for UDP traffic and port 22 for SSH traffic:
$ sudo ufw allow 1194/udp $ sudo ufw allow OpenSSH
Restart the firewall:
$ sudo ufw disable
$ sudo ufw enable
Start the OpenVPN service:
$ sudo systemctl start openvpn
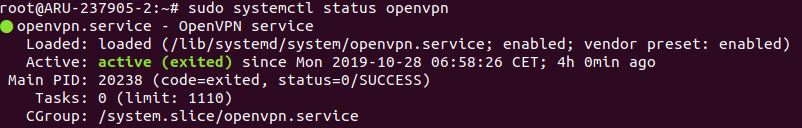
Check the status of the service. If everything was successful, the screen will look like the one shown here.
$ sudo systemctl status openvpn
Run the service when the Server is switched on:
$ sudo systemctl enable openvpn
Create the basic configuration for Clients:
$ sudo mkdir -p ~/client-configs/files
$ sudo cp /usr/share/doc/openvpn/examples/sample-config-files/client.conf ~/client-configs/base.conf
$ sudo nano ~/client-configs/base.conf
Find the "remote" section and check that it reads "remote IP_Server 1194"
- IP_Server: Enter the Server IP
- 1194: port selected earlier.
Find the "proto" section to check that the Server is set to UDP (you will find the TCP line commented with a ";").
Go to the "user" and "group" sections and remove the ";" to "uncomment" them.
Go to the "ca.crt" - "client.crt" - "client.key" - "ta.key" sections and comment with a"#" at the start of each line.
Go to the "cipher" section and add the command "auth SHA256" under the command "cipher AES-256-CBC".
Add the command "key-direction 1", wherever you like.
Add these commented lines somewhere. If the Client is a Linux machine, these need to be uncommented.
# script-security 2
# up /etc/openvpn/update-resolv-conf
# down /etc/openvpn/update-resolv-conf
Save and exit.