Once the first stage of installing OpenVPN is complete, the certificates and keys required to access the VPN must be generated.
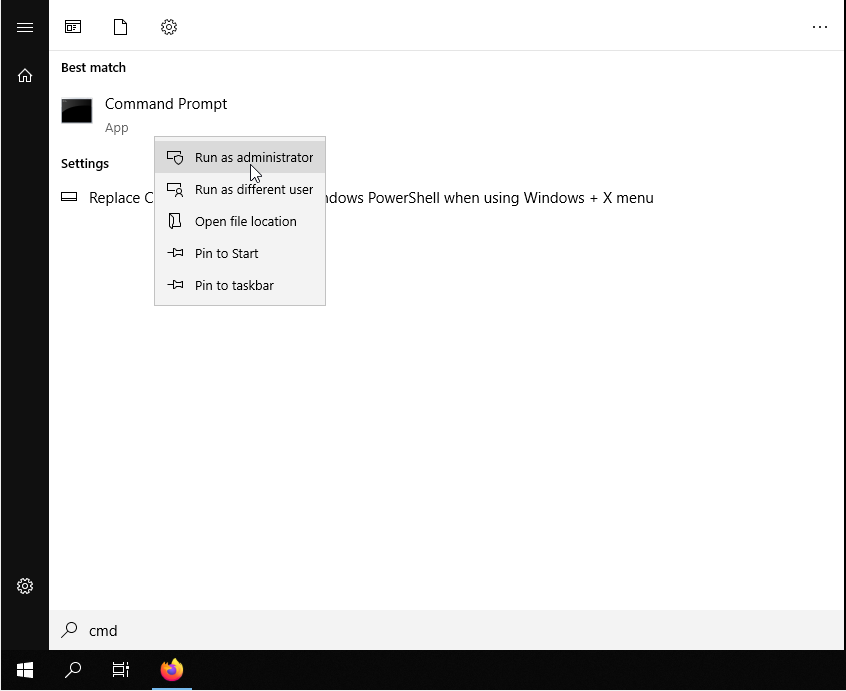
First, open your Windows Server terminal. To do this, click on Start, type "cmd" and right click on the Command Prompt icon, then select "Run as administrator".
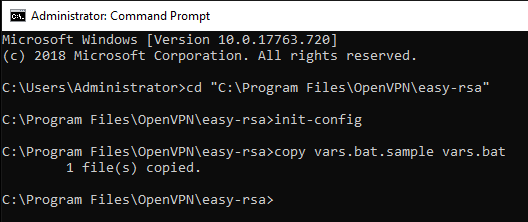
Go to the folder in which you have installed OpenVPN and run the script "init-config".
cd "C:\Program Files\OpenVPN\easy-rsa"
init-config
This should return an output similar to the one shown above.
At this point, you need to make changes to the "vars.bat" file in the "C:\Program Files\OpenVPN\easy-rsa" folder:
notepad vars.bat
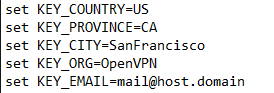
Almost at the end of the document you find a series of lines starting with "set" which are used to set some of the variable environment data. Edit these fields with your own information to generate the certificate.
This step is not vital as you will be required to enter this information later but, by setting these values here in this file, you will ensure that they are used as default parameters in future.
Once you have entered this information, save the file and close the text editor. Type the following command to implement the changes made:
vars
clean-all
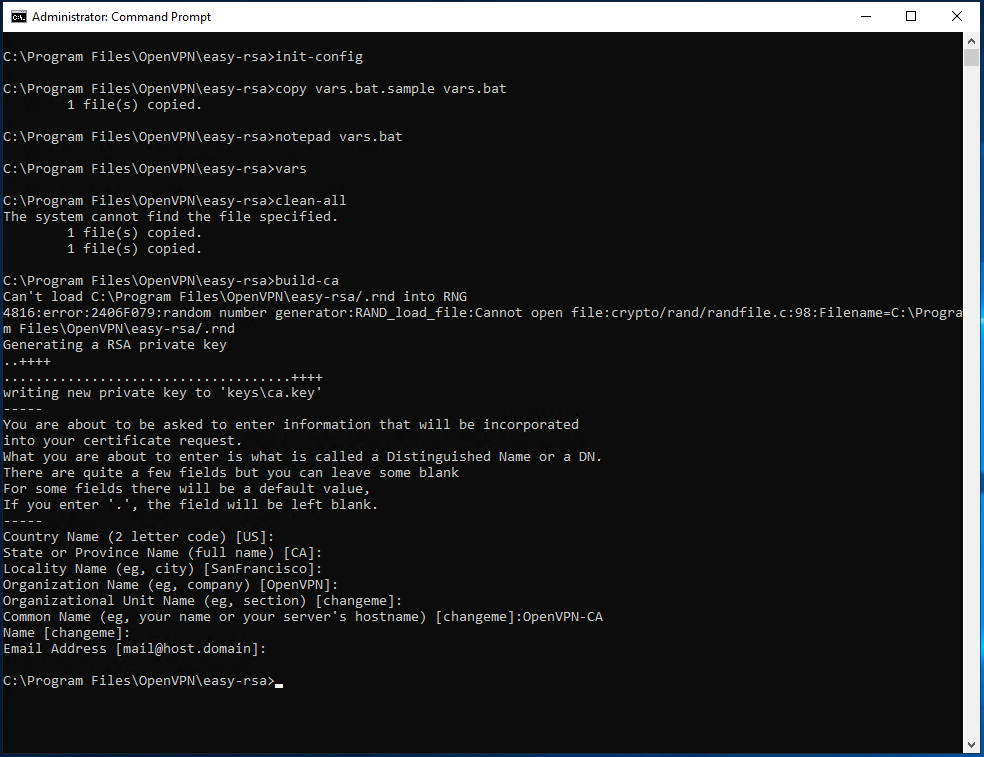
Next, start creating the Certificate. From terminal (run as administrator, still in the "C:\Program Files\OpenVPN\easy-rsa" folder) type:
build-ca
If you have already edited the "vars" file with your details, these will appear in the square brackets of each required field. In this case, simply press "Send" to set these values as default parameters.
In the "Common name" field, however, you must assign an easy to remember name: in this case "OpenVPN-CA"will be used.
When the successful generation of the certificate has been confirmed, the "ca.crt" and "ca.key" files will be created in the "easy-rsa\keys" folder.
At this stage, keys must be created for the server, which can be started using the command:
build-key-server server_name
In this case, in the "Common Name" field, you must specify a generic name for the server. As you can see below, in our case the name "server" has been used.
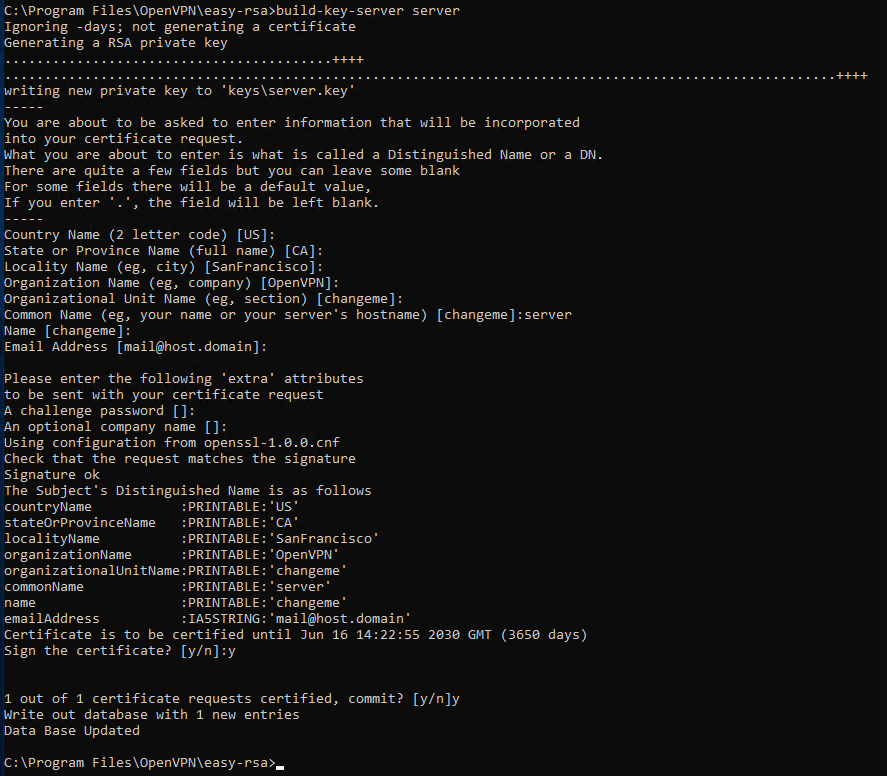
Towards the end of the procedure you will be asked twice to confirm that the data should be saved as entered. Type
y both times and press "Send".